Author Jinali Pabasara

Welcome to the second article in our series, where we explore fundamental networking concepts in AWS. So far, we’ve set up our Virtual Private Cloud (VPC), and inside it, we’ve created two subnets — one is private, and the other is public. But here’s the thing, right now, both of these subnets are pretty much the same. They are both private and can’t connect to the internet from the outside.
Our aim is to configure things so that specific resources within the public subnet can freely communicate with the internet when needed. On the other hand, we want to ensure that the resources residing in the private subnet remain completely secured and isolated from the internet.
Internet Gateway and Route Tables
An Internet Gateway serves as the gateway for resources within a VPC to access the Internet. To set it up, we create the Internet Gateway separately and then attach it to our VPC. Keep in mind that Internet Gateways are not automatically connected to any VPC; they remain independent components until linked to a specific VPC.
However, simply having an Internet Gateway in place isn’t enough to grant Internet access to our resources. We also need to configure a route table. By setting up the appropriate routes in the route table, we allow resources within the VPC to effectively connect to and utilize the internet through the Internet Gateway.
Before creating the Internet Gateway and Route table, let’s go ahead and launch an EC2 instance into our Public Subnet.
Launching an EC2 instance to the Created VPC
Go to the AWS Management Console and navigate to the EC2 service. Click on “Instances” from the left-hand menu. Click on the “Launch Instance” button to start the instance creation process.

Now, on the “Launch an Instance” page, it’s time to give a friendly name to our instance. This name will help us easily identify and manage the EC2 instance later on.

Leave all the other settings unchanged and scroll down to the Network Settings. Then, simply click on the Edit button to make updates to the Network Settings.

By default, AWS automatically chooses the Default VPC for your instance. However, since we want to use the VPC we created in the previous step, simply click on the drop-down menu under the VPC field and select our custom VPC from the list. This ensures that the EC2 instance will be launched within the VPC we specifically set up.
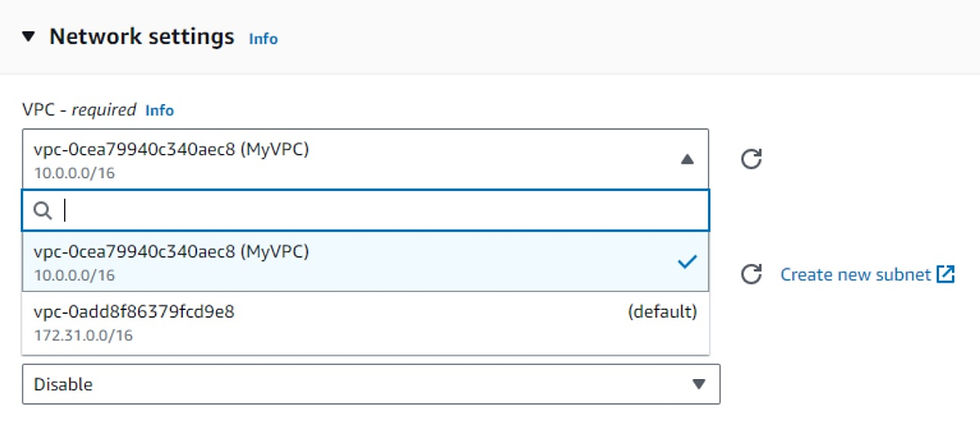
Now, the next step is to choose the Subnet where we want to deploy our instance. To do this, you’ll find a dropdown menu under the Subnet section. From that menu, select the PublicSubnet that is associated with our VPC. This ensures that our EC2 instance will be placed within the PublicSubnet which we created earlier.

In order to enable internet access to our EC2 instance, we must assign a Public IP address to it. From the drop-down menu for the “Auto-assign Public IP” field, select “Enable” to assign a Public IP address to the EC2 instance.

Keep all the other settings unchanged, and simply click on the “Launch Instance” button to initiate the instance launch process.

After launching the EC2 instance, allow it a moment to update its status and transition to the “running” state. Once the instance is up and running, proceed by selecting it.
Now, you’ll be able to view all the relevant details of your EC2 instance. Since we intend to access the instance through the internet, you can find the public IP address assigned to the instance. Additionally, notice that the Private IP address of the EC2 instance falls within the range of our Public Subnet’s CIDR range.
It’s worth mentioning that this EC2 instance has been successfully launched within the VPC we created earlier, and it now resides in the public subnet as we had instructed during the setup.

Now let's try to SSH into our instance. For that select the EC2 instance and click on the connect button at the top of the page.

From the Connection options select the EC2 instance connect and click on the Connect button to SSH into the EC2 instance.

However, after some time, you might encounter an error message indicating that SSH access to your EC2 instance is not possible. So, what could be the reason behind this issue? Despite placing the instance in the public subnet and assigning a Public IP address to it, we are still unable to establish an SSH connection to the instance.

The reason behind this is that even though we have assigned a public IP address to our resources, we haven’t configured an Internet Gateway and a Route table to properly handle incoming traffic from the Internet and allow access to the resources within the public subnet.
Now as the next step, we can move forward with setting up the Internet Gateway and Route table to grant it Internet access. This will allow us to connect to the instance from the internet as planned.
Creating an Internet Gateway
Head over to the VPC page in the AWS Management Console. In the left pane, locate and select “Internet Gateways.” Once there, click on the “Create Internet Gateway” button to initiate the creation process for a new Internet Gateway.

On the creation page, provide a suitable name for the Internet Gateway, and then simply hit the create button.
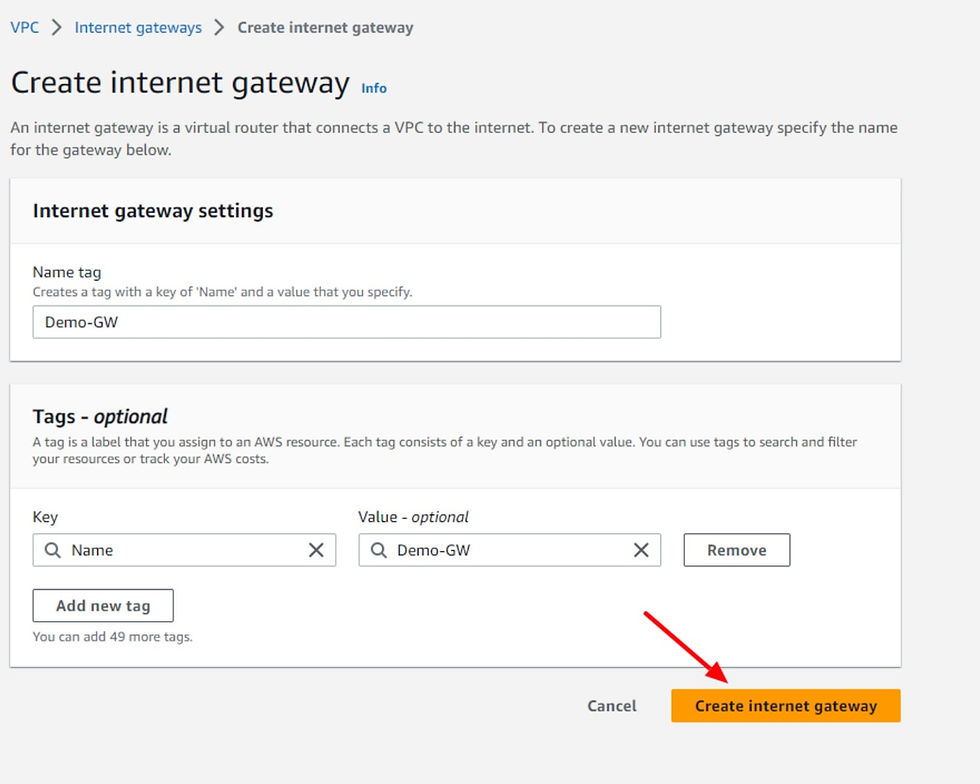
Once the Internet Gateway has been created, select the created gateway from the list. There we can see that the state of the gateway is not attached to a VPC.

To connect the previously created gateway to our VPC, find the gateway in the list and select it. Next, click on the “Actions” button located in the top menu. From the drop-down menu that appears, choose the “Attach to VPC” option. This will initiate the process of associating the Internet Gateway with our VPC.

Choose the VPC that we previously created from the list of available VPCs. After selecting it, simply click on the “Attach” button to associate the Internet Gateway with the chosen VPC.

Now, if we go back and check the Gateway we just created, we’ll notice that its state has been updated to “Attached,” indicating a successful association with the VPC we previously set up. This means the Internet Gateway is now ready to handle internet traffic for resources within our VPC.

A key point to remember is that a VPC can only be associated with one Internet Gateway, and conversely, a specific Internet Gateway can only be linked to a single VPC.
Creating Route Table
To set up a route table, access the AWS Management Console, and click on the “Route Tables” option from the left-hand menu. There, you’ll find a list of all available route tables. As you’ll notice, there’s a Main Route Table associated with our VPC by default.
However, it’s a good practice to create two additional route tables — one for the public subnet and another for the private subnet. To create these new route tables, simply click on the “Create Route Table” option.

Let’s give the route table a name on the route table creation page, and don’t forget to select the VPC we previously created from the drop-down menu. Once that’s done, go ahead and hit the “Create route table” button to create the route table.

Let’s replicate the steps to create a route table for the Private subnet as well.
In other words, you’ll need to follow the same procedure we used earlier to set up the route table for the Public subnet, but this time, we’ll create a new route table specifically for the Private subnet.
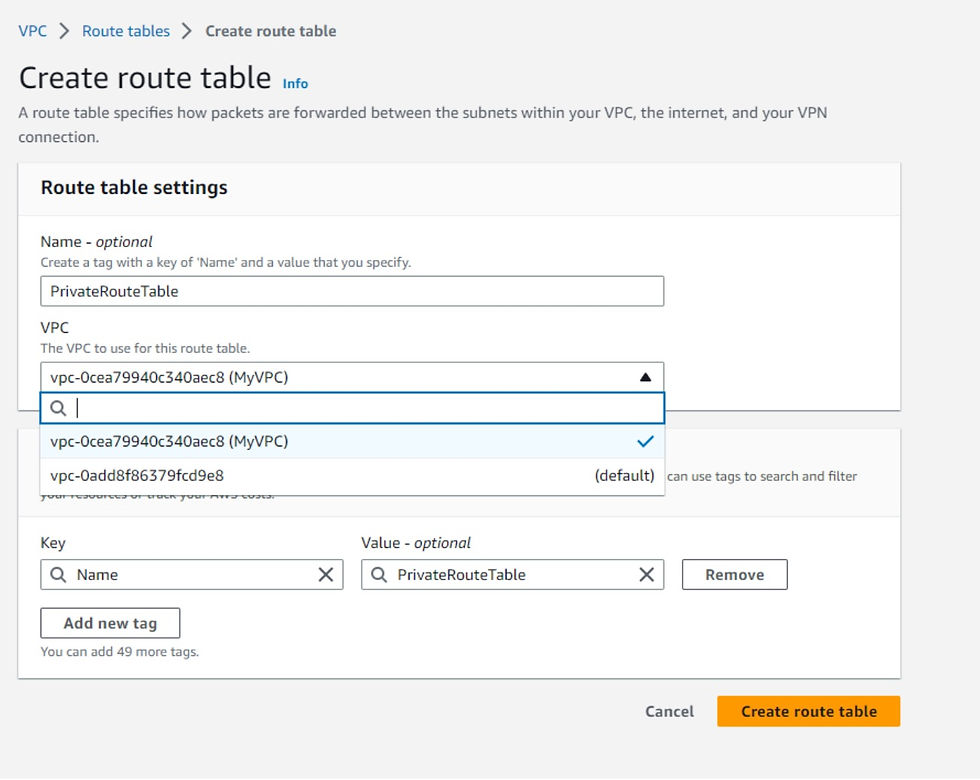
Now, we can observe the list of both route tables we created, and they are now associated with our VPC.

Now, let’s associate our subnets with the route table we created.
To proceed, we’ll need to access the list of Route tables and select the Public Route table. Once selected, we’ll head to the subnet association section. Within this section, we’ll specifically look for the explicit subnet association option and click on the “edit” button.

Great, now let’s take a look at all the subnets within our VPC. To attach the Public Subnet to the Public Route Table, simply select the Public Subnet from the list, and then click on the “Save” button. By doing this, we explicitly associate our Public Subnet with the Public Route Table we previously created.

Let’s proceed with the same steps to explicitly associate the private subnet with our private route table, as outlined below.

If we return to the route tables page, we’ll notice that both our public and private subnets are now connected to their respective route tables.

If we take a look at our Public Route table and check its routes, we’ll see a list of routes associated with this table. Currently, there is only one route defined.
These routes play a crucial role in guiding the traffic flow from our subnet. In this particular case, the route we have specifies the destination as the CIDR range of our VPC. What this means is that by default, any IP address within our VPC will be directed to the VPC itself.

Now to allow traffic from the internet to our public subnet we can create a new rule. To do that click on the edit Rule button. From the edit page click on the Add Route button.

Afterward, choose the destination “0.0.0.0/0” in the route table and select the “Internet Gateway” as the target.
By specifying “0.0.0.0/0” as the destination, we are effectively instructing the route table to route all IP addresses. This means any traffic destined for locations outside our VPC’s IP range (in this case, “10.0.0.0/16”) will be directed to the Internet Gateway we previously set up.

Afterward, simply click the “Save” buttons to apply the rule.

Now, if we navigate back, we’ll notice that the newly created rule has been added to the list of rules. It’s now visible among the other existing rules.

Now, let’s revisit the EC2 instance we attempted to SSH into earlier. During our previous attempt, we encountered an error and couldn’t establish a connection. However, if we try to SSH into the EC2 instance again now, you’ll notice that we can successfully connect.

The reason behind this success lies in the fact that all the internet traffic directed toward the Internet Gateway associated with our VPC is now efficiently routed to the Public Subnet. As our EC2 instance is situated within the public subnet and has a public IP, we can conveniently access it from the internet.
In simpler terms, the proper setup of the Internet Gateway and the associated routing configuration now allows external traffic to find its way to our EC2 instance, making it accessible from the Internet.
Wrapping Up
Let’s take a look at what we’ve accomplished thus far. We successfully launched an EC2 instance within our public subnet. Following that, we set up an Internet Gateway and a route table to ensure that Internet traffic can reach our public subnet. As a result, our EC2 instance now has internet access, and we can conveniently SSH into it from the internet.

Throughout this article, we delved into the concepts of Internet Gateways and route tables, understanding their role in facilitating access to resources within a public subnet via the Internet.
In the next article, we’ll explore additional networking concepts and uncover methods for accessing resources within a private subnet without the need for a direct internet connection. Stay tuned to learn more about building a secure and well-connected network environment in AWS!
About the Author: Jinali Pabasara is a Software Engineer who has a strong passion for cloud computing. Sge finds great satisfaction in sharing the programming and cloud computing concepts knowledge that she has gained during her learning journey.

Comments