Game Theory Applications In Cyber Security
- abdelsyfane
- Jul 27, 2020
- 7 min read
Author Casey Allen

Information assets are under constant threat of cyber-attack. According to researchers from the University of Maryland Clark School of Engineering such attacks occur every 39 seconds (Cukier, 2007). The perpetrators of these attacks do not discriminate in terms of who they target. Businesses both large and small, public sector agencies at every level of government, non-profit and religious organizations, and even individuals themselves are targets of interest for cyber criminals. As the likelihood and impact of cyber-attacks continues to rise organizations have begun to realize the necessity of investing in skilled professionals and robust technological controls to protect their digital assets. The principles of game theory “can offer insights into any economic, political, or social situation that involves individuals who have different goals or preferences” (Myerson, 1997). The broad applicability of its principles makes game theory an effective Rosetta Stone for technical and non-technical stakeholders alike to evaluate cyber defense strategies.
In game theory, any “game” will consist of two or more rational players whose actions are determined based on whatever strategy maximizes the payoffs they can expect to receive from playing the game. A “player” may be in individual, but for the purposes of exploring game theory principles as they relate to cyber security we can also think of a player as a team, or a collective of individuals united by their efforts in pursuit of a common goal. Let’s look at an example game where Player 1 is Team Defense, the cyber security professionals within a legitimate business (Company X) whose job it is to protect the organization’s information assets, and Player 2 is Team Offense, a criminal enterprise intent on compromising those same assets. We can visualize this game using a simple matrix where the strategies of Player 1 are shown as rows and the strategies for Player 2 are shown as columns. At the intersection of each player’s strategies the payoffs (E) are shown with Player 1’s value on the left and Player 2’s on the right:

Each player in our example game has two strategies to choose from. Team Defense must choose whether to implement a security control to protect an information asset (Strategy A) or to accept the risk of attack unmitigated (Strategy B). Team Offense must choose whether to attack that same asset (Strategy C) or to leave it alone (Strategy D). For the purposes of our example game we will assume that if Team Defense chooses to defend the asset it will be successful. Likewise, we will assume that if Team Offense attacks an undefended asset it will be successful.
Using our knowledge of the game’s players we can make some assumptions as to the various kinds of tradeoffs each player may consider when selecting their strategy. We can summarize the factors Team Defense will consider when choosing its strategy as follows:
• Value of the asset to the organization
• Building and maintaining consumer trust
• Legal and regulatory compliance
• Resources required for implementation and maintenance
• Usability (ease with which legitimate users can perform their work)
Similarly, we can summarize some of the factors Team Offense will consider when choosing its strategy:
• Value of the asset if compromised
• Resources required to execute an attack
• Specialized skills required to plan and execute an attack
• Importance of keeping their custom-built exploits (TTP) a secret
• Risk of being caught (fines, incarceration, etc.)
Although this is an extremely oversimplified example of how cyber warfare games play out in real life the logic of how game theory principles can be useful in making strategic decisions is beginning to take shape. Now that we have our players and strategies defined, we can begin to examine what the payoffs for each player might look like in our example game:

We can use the row and column names of our matrix to refer to each of the possible outcomes of this game. In the (Defend, Attack) game Team Defense chooses to implement a control to protect an information asset, and Team Offense chooses to attack it. As a result of these strategies Team Defense earns 50 points, while Team Offense suffers a loss of -5. Using our summaries of how each player determines the value of possible outcomes we can see how this result makes sense. The Defend strategy for Team Offense is advantageous because it prevented that asset from being compromised. The implementation of this security control has the added benefit of fulfilling one or more compliance requirements. The result of the (Defend, Attack) game is less advantageous for Team Offense who exhausted a significant amount of resources attempting the attack but were ultimately unsuccessful. The (Defend, Attack) game is therefore the worst-case scenario for Team Offense.
In our example game the payoffs for the (Defend, Don’t Attack) game are 25 for Team Defense and 0 for Team Offense. In this game Team Defense again chooses to implement a security control to protect an information asset, but Team Offense chooses not to attack it. The security control made the asset more difficult for legitimate users of Company X to use, but it did satisfy one or more compliance requirements. For Team Offense the (Defend, Don’t Attack) doesn’t cost them anything, but it doesn’t earn them anything either.
The (Don’t Defend, Attack) game is the worst-case scenario for Team Defense. In this game Team Defense chooses not to implement a security control to protect an asset, and Team Offense is able to execute a successful cyber attack to compromise it. As a result of this game the payoff for Team Defense is -100. Team Offense, on the other hand, will walk away from the (Don’t Defend, Attack) game celebrating their payoff of 25. The (Don’t Defend, Attack) game is the best-case scenario for Team Offense.
In the (Don’t Defend, Don’t Attack) game Team Defense chooses not to implement a security control to defend the asset, and Team Offense chooses not to attack it. Team Defense is rewarded with 50 points for saving the time, money and effort required to implement the security control and for not interfering with the normal business operations of Company X’s users unnecessarily. Team Offense walks away with a payoff of 0 as this is once more a game that cost them nothing to play, but in return they get what they pay for: nothing.
Now that we understand the payoffs for both players in each of the four possible outcomes let us use our matrix to visualize the ideal strategies of each player in response to the strategies of the opposing side. In the matrix below Team Defense’s best responses are highlighted in yellow, while Team Offense’s best responses are highlighted in green:

In our example game the ideal strategy for Team Defense is to defend the asset when Team Offense chooses to attack it, and to not defend the asset when Team Offense chooses not to. Conversely, the ideal strategies for Team Offense are to attack when Team Defense does not defend the asset, and to not attack the asset when Team Defense chooses to defend it. Neither player has a strategy which maximizes their payoffs regardless of the opposing player’s strategy, and none of the four possible outcomes of this game results in a stable outcome where neither player has an incentive to change their strategy to further improve their payoffs. To maximize their expected payoffs in this example game each player must choose to randomize their strategies. Rather than flipping a coin to determine which strategy to choose we can use game theory principles to determine the frequency with which each player should select each of their strategies to maximize their expected payoffs.
Let p be the probability Team Defense will defend the asset, and q be the probability Team Offense will attack it. By solving for p and q we can see the ideal mixture of strategies for each player that maximize their respective payoffs regardless of whatever strategy the opposing side chooses when playing the game:
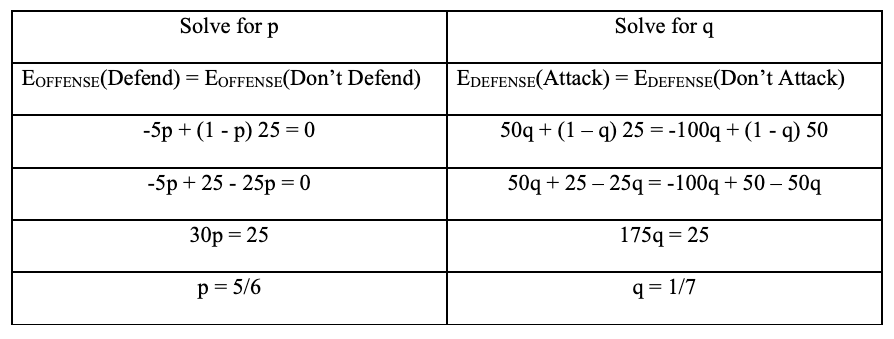
Based on the values of p and q we have determined that if both players choose to randomize their strategies such that Team Defense chooses to defend the asset 5 out of 6 times and Team Offense chooses to attack the asset 1 out of 7 times both sides will maximize their respective payoffs for this game.
By calculating the expected payoffs for each player based on how frequently the game will result in each of the four possible outcomes we can calculate how much each player can expect to earn if they choose to play this game. To determine how often the game will result in each of the four outcomes we use the cross products of each player’s ideal mixture of strategies:

Now that we know how often the game will result in each of the four possible outcomes, we can calculate the expected payoffs for each player if they choose to play the game:

The results of this example game are significant because they show Team Offense can expect to earn nothing by choosing to play. In a real-world scenario this means Team Offense is likely to leave Company X alone and bother somebody else instead.
As quickly as the cyber landscape is changing, we can expect the payoffs of cyber warfare games to be dynamic. The value of information assets will fluctuate as new technologies are brought to market and existing systems age into obsolescence. Changes in the economy, political landscape, consumer trends, and legal and regulatory compliance requirements can all impact the players’ calculations of expected value for playing such games. For Team Defense to maintain their advantage they must adopt a process of continuous improvement. An accurate inventory of all information assets classified according to their value to the organization is critical for assessing the severity of risk to them. Using the principles of game theory cyber security professionals should then implement those controls which lower the risk to their information assets to an acceptable level while maximizing their returns on investment.
References
Cukier, M. (2007, February 9). Study: Hackers Attack Every 39 Seconds. Retrieved from University of Maryland: https://eng.umd.edu/news/story/study-hackers-attack-every-39-seconds
Myerson, R. (1997). Game Theory: Analysis of Conflict. Harvard University Press.
Casey Allen is a Certified Information Systems Security Professional (CISSP) and holds a Master of Cybersecurity and Leadership degree from the University of Washington. He is currently serving as Security Governance, Risk and Compliance Manager for the Philips HealthSuite Digital Platform. Connect with Casey on LinkedIn.




Game theory has diverse applications across various fields, from economics to biology. In economics, it helps analyze competitive strategies and market behaviors, guiding businesses in decision-making processes. Here, concepts from game theory can be employed to evaluate strategies that promote integrity, such as assessing platforms like totogood (먹튀검증) to validate their legitimacy. Additionally, it finds relevance in evolutionary biology, where strategies affect species survival and reproduction. In political science, game theory assists in understanding conflict resolution and cooperation between nations. One intriguing application involves the online gaming industry, where ensuring fair play is crucial.